Which of the Following May Indicate a Malicious Code Attack
This compromises the security of the software because it may be possible to inject malcode into runtime memory. Malicious code can be spread by downloading corrupted email attachments and files or visiting infected websites.
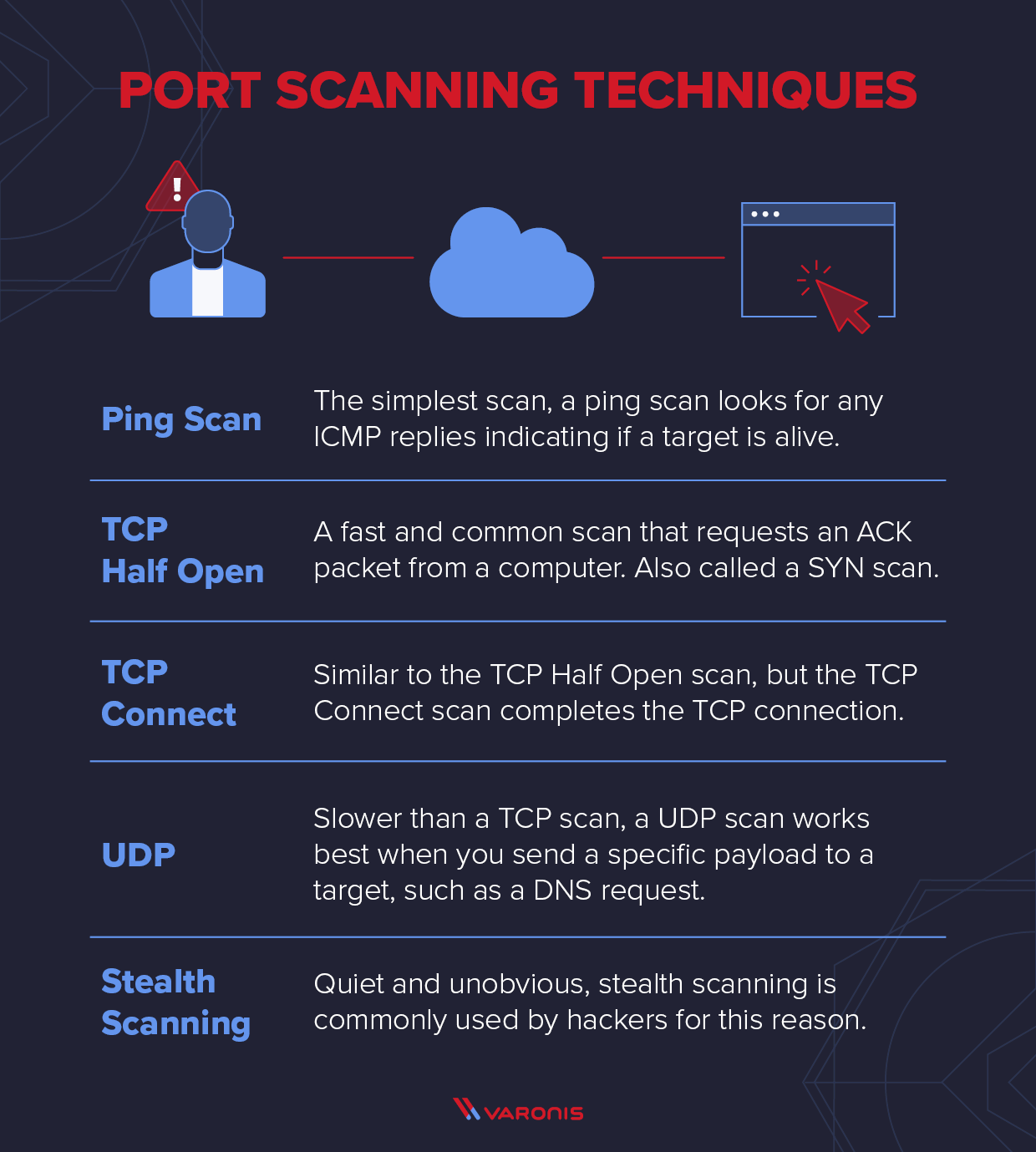
What Is A Port Scanner And How Does It Work
Malicious code Behaves in an unexpected way by its designer or user through the intention of programmer.

. Malicious Code - Social Engineering Knowledge Check What is a common method used in. What is an indication that malicious code is running on your system. Then it spreads when an unsuspecting end-user or automated process executes the program.
Malwarebytes regards browser hijacker malware to be among the top ten malware attacks targeting businesses today. Assignment Requirements Select a well-known virus or malicious code attack and write a summary report explaining what kind of malicious attack it was how it spread. A virus is a malicious piece of code that binds itself within the code of another legitimate program.
Java Applets ActiveX Controls Scripting languages Browser plug-ins Pushed content Once inside your network or workstation malicious code can enter. They can damage or compromise digital files erase your hard drive andor allow hackers access to your PC or mobile from a remote location. A highly sophisticated worm that was discovered in 2010.
Most Common Layer 2 Network Attacks. Summary Report on a Malicious Code Attack Learning Objectives and Outcomes You will learn how to mitigate the threat of a virus or malware attack. Malicious code includes viruses trojan horses worms macros and scripts.
Up to 20 cash back Visiting infected websites or clicking on a bad email link or attachment are major gateways for malicious code to sneak its way into your system. Malicious Code Examples of Buffer Overflow. Trojan horse A program that appears to do something non-malicious.
This answer has been confirmed as correct and helpful. Indicate how you would prevent the attack from recurring on a network you control. A common type of malicious code is the virus which is a little program attaching to other programs or files and will copy itself in a computer and even spread to other networked computers.
It occurs when a program writes data outside the boundary of its allocated memory. A pop-up window that flashes and warns that your computer is infected with a virus. Expert answeredhoudPoints 400 Log in for more information.
Types of Network attacks. The goal of a ransomware attack is to gain exclusive control of critical data. Assignment Requirements Research and select a well-known malicious code attack that occurred within the last year.
What type of exploit did this attacker engage in. While an advanced persistent threat APT may leverage any of these attacks they are most closely associated with zero-day attacks. Since they can modify the host files viruses can cause harm to the applications core functionality lock users out of their machines or corrupt sensitive files.
A computer virus is a type of malicious application that executes and replicates itself by injecting its code into other computer programs. Malicious Codes Attacks. File corruption What is a possible indication of a malicious code attack in progress.
Denial of Service DoS Attacks. Worm Virus and Trojan horse. Buffer overflow is a well-known security vulnerability.
The hacker encrypts and holds your data hostage and then demands a. Can do much harm. Antivirus software that features automatic updates malware removal capabilities Web-browsing security and the capability to detect all types of infections are the best defense.
Write a summary report explaining what kind of malicious attack it was how it spread and attacked other devices and how it was mitigated. For instance several types of malicious code can be found online in Java applets scripting languages ActiveX controls browser plug-ins and pushed content. 3 Malicious Code.
Worms are pieces of malicious code making copies of itself. Hard to detect. Updated 1222020 92456 PM.
ACLs Network Security Network Troubleshooting. Types of Malicious code Viruses Programs that can spread malicious code to other programs by modifying them. Bens system was infected by malicious code that modified the operating system to allow the malicious code author to gain access to his files.
It searched for unprotected administrative shares on the local network exploited zero day vulnerabilities in Windows Server and Print Spooler services connected to systems using a default database password or spread by infected USB drive. Select a well-known virus or malicious code attack and write a summary report explaining what kind of malicious attack it was how it spread and attacked other devices and how it was mitigated. 7 Examples of Malicious Code.
Here are the 15 most common types of Internet security issues or web security problems and some relevant steps you can take to protect yourself your data and your business. You may use the Internet for research. Malicious code can take the form of.
All of the following are examples of malicious code except. Asked 1222020 21521 PM. Unit 9 Assignment 2.
Indicate how you would defend the attack from recurring on a network you control. Escalation of privilege B. Keyloggers also known as system monitoring or keystroke loggers are malware types created to monitor and record all the keystrokes on an infected computers keyboard.
Viruses can range from being relatively harmless to causing significant damage to a system. The code gives a cybercriminal unauthorized remote access to the attacked system called an application back door which then exposes sensitive company data according to cybersecurity and antivirus. Which one of the following techniques is most closely associated with APT attacks.

Social Engineering Attacks Techniques And Countermeasures Field Effect Software Inc

Developing Petya Ransomware Attack Goes Global Targets Merck In Us Cyber Security Cyber Attack Wordpress Security

Malware Attacks Definition And Best Practices Egnyte
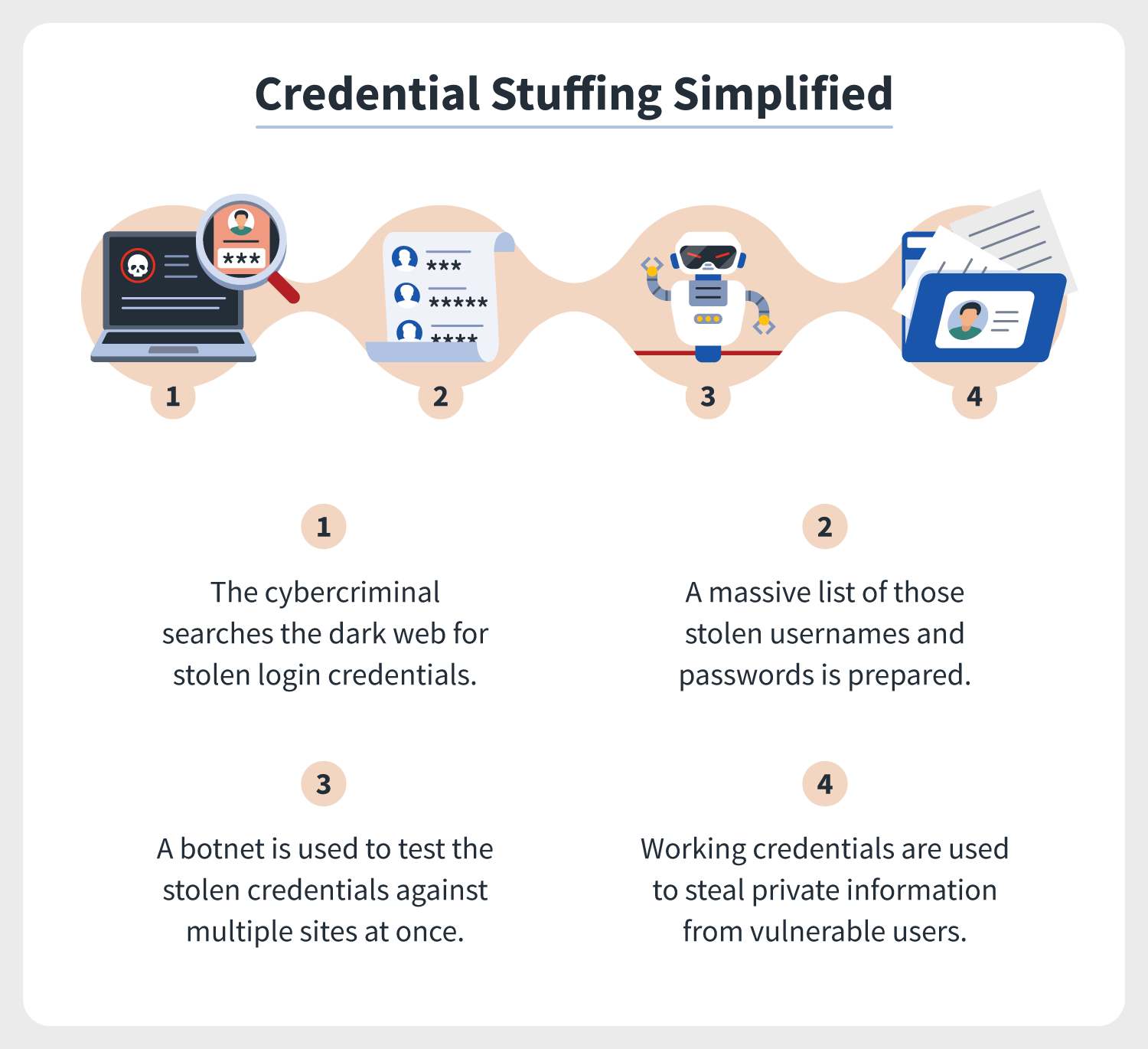
Credential Stuffing Simplified Attack Protection Tips Norton
No comments for "Which of the Following May Indicate a Malicious Code Attack"
Post a Comment